Do you know how to Use Two-Factor Authentication Correctly? One of the most excellent two-factor authentication solutions can be used even if you don’t have a phone. Take a look at these alternatives.
Whether you’re prepared or not, you should start thinking more about two-factor authentication.
Online security using a combination of a standard password and a secondary number code, required on any device you haven’t signed in previously, is known as two-step authentication, multi-factor authentication, or 2FA for short. Someone who obtains your password won’t be able to access your account unless they also get access to your phone, where you’ll generally receive the verification code (and know how to unlock it).
Some tech companies have started mandating two-factor authentication (2FA) because the extra hassle is justified by its added protection. Two-factor authentication (2FA) is now required for Google accounts and Amazon’s Ring, and it is enabled by default for most Apple IDs.Amazon sends a text message link to click on when you log in from a new device to selectively implement two-factor authentication (2FA) on its apps and website.
Despite these advances, the most effective method of implementing two-factor authentication (2FA) does not involve a purely reactive stance. Two-factor authentication (2FA) techniques that rely on sending a code to your phone are preferable to nothing, but SIM hijacking attacks can still compromise them. (The FCC has only begun looking into this issue.)If your phone is stolen, have a backup
Here are some choices to think about if you’re ready to commit to two-factor authentication:
Table of Contents
Download a Two-factor Authentication App

Furthermore, in the discussion of how to Use Two-Factor Authentication Correctly? Most significant websites now allow you to utilize an authenticator app to produce 2FA codes directly from your phone rather than receiving text messages with these codes. After you have linked the authenticator app to your online service (often by scanning a one-time QR code), you will be able to use it to look for a code whenever you log in. This can be accomplished by checking the QR code on the authenticator app.
Though Google and Microsoft have authenticator apps compatible with many websites, Authy meets all my needs. It’s costless, and what’s more, you may set it up on an unlimited number of gadgets simultaneously. My two-factor authentication tokens are always at my fingertips thanks to the Authy apps I have loaded on my iPhone, Android phone, iPad, Windows desktop, Windows laptop, and Mac Mini.
As with other luxuries, though, this one comes with a price. When setting up Authy on a new device, a unique authentication code is needed; this code is sent to the user through a text message from Authy. Two of Authy’s safeguards against this, however: Are backups on a new device require a password, and you can turn off Authy installation at any time. You’ll need physical access to a device with Authy installed to toggle the feature back on.
If you have a history of forgetting passwords, you should rely on something other than Authy because its password is unrecoverable. Its multi-device support, though, makes it easier to beat if you need to have access to 2FA codes on a variety of devices in addition to your computer.
Substitute App- or Email-Based 2FA With Text-Based Methods.
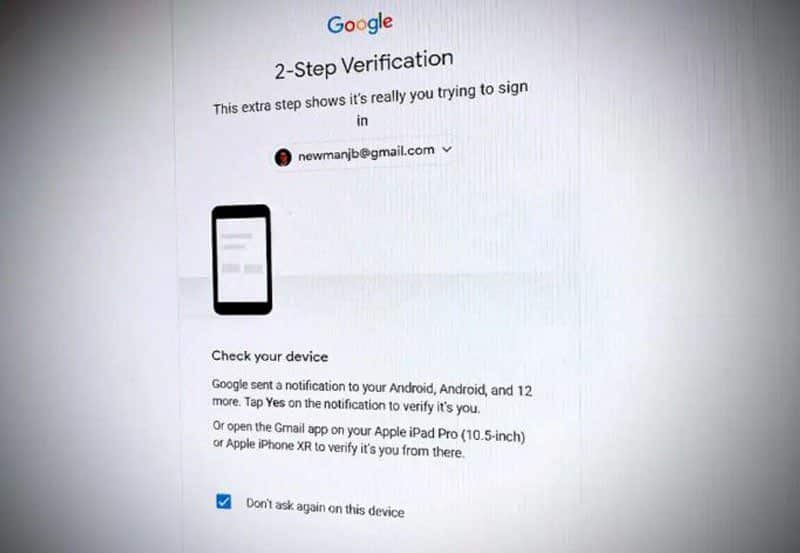
For example, if you’ve ever logged into Gmail on a new device and been prompted with “Are you trying to sign in?” on your phone, you’ve already experienced a type of two-factor authentication (using an existing sign-in on one device to help you sign in on another). Some services email a verification number when you login in on a new appliance.
Both methods are preferable to receiving codes by text message, provided that your mobile devices and email account are safe. They can also be used in tandem with an authenticator app like Authy. Thus, when 2FA is activated, you can access your accounts using various means.
For Added Safety, You Can Use Printed Codes or a Security Key.

You can use two-factor authentication (2FA) to keep your account safe by printing off backup codes or connecting a USB security key to your device. For example, I linked a Yubico security key to my Gmail, Microsoft, Twitter, and Stripe accounts last year so that I can bypass the requirement for Authy if I need to log in to any of those services on a new device. Yubikey-compatible services are listed below.
When Using a Computer, Please Use a Google or Apple Account.
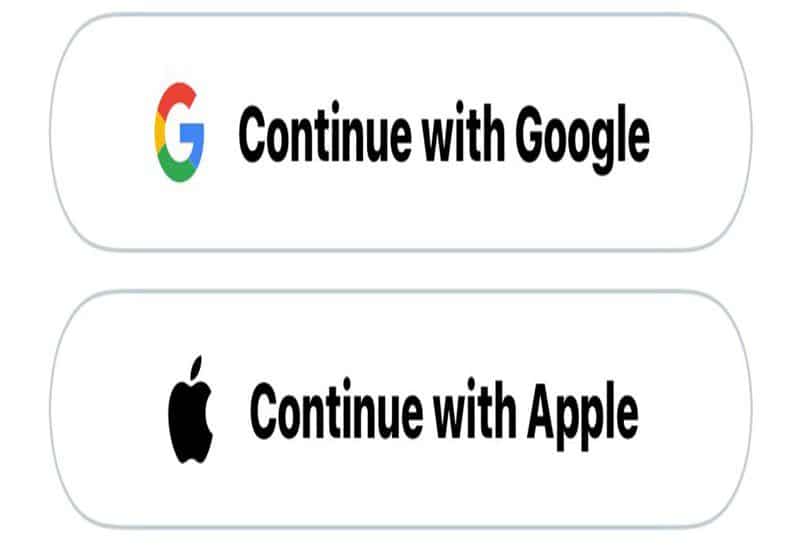
If a site allows you to sign in using your Google or Apple account, you should do so after you’ve taken the time to secure those accounts. When a website asks me to “Sign in,” I frequently use “Sign in with Google” since it prevents me from remembering yet another password and provides the same degree of protection as my Google account.
Establishing The Stage

This is where we have some difficulty: Note that the choices above may only be compatible with some apps and internet services. Some may only support the use of physical security keys or email-based authentication. Conversely, some may not offer printed codes as a backup option. Some providers may not provide two-factor authentication, while others only offer it in text.
It would help if you respected 2FA because of that. Instead, you should prioritize the accounts that store your most vital information by upgrading their security to the highest level possible. Strong passwords, ideally those generated by a password manager, become even more crucial without 2FA choices.
Are you prepared to launch? Quickly activate two-factor authentication on Google, Microsoft, Yahoo, Amazon, Facebook, Twitter, LinkedIn, and Apple by clicking the appropriate link below. Authy also provides a searchable library of guides on implementing 2FA on several other platforms.
If you want to read more about how to Use Two-Factor Authentication Correctly? Click here.




